The TAS Vibe | IAM Best Practices & Security Insights
Discover IAM best practices for 2026, including adaptive authentication and zero-trust strategies to secure SMBs and enterprises against modern cyber threats.
TECHNOLOGY
The TAS Vibe
1/5/202615 min read
My post content
IAM Best Practices 2026: Mastering Adaptive Authentication & Zero-Trust Strategy for SMBs and Enterprises


Section 1: Introduction & Hook
Why Identity & Access Management Is No Longer Optional in 2026
In 2025 alone, compromised credentials drove a 160% increase in security breach incidents, and today, one out of every five data breaches starts with stolen or misused identities. This single statistic reveals a harsh reality: attackers no longer “hack” systems—they simply log in. As organizations accelerate digital transformation, identity has quietly become the weakest link in modern cybersecurity.
For years, businesses relied on password-only authentication and static access rules to protect critical systems. That approach is now obsolete. Passwords are reused, phished, brute-forced, or sold on the dark web within minutes. Meanwhile, static access controls fail to adapt to real-world conditions such as remote work, cloud environments, third-party vendors, and privileged users. These gaps create dangerous blind spots—areas where organizations have little to no visibility into who is accessing what, from where, and at what time.
The consequences are no longer theoretical. Regulatory bodies are enforcing stricter compliance standards, and failures are expensive. In one high-profile case, T-Mobile faced penalties exceeding $60 million under NYDFS regulations, demonstrating how identity-related security failures can directly impact revenue, reputation, and shareholder trust. Similar enforcement trends are emerging globally, making identity governance a board-level concern rather than a backend IT issue.Write your text here...
What This Guide Will Deliver
By the end of this guide, you will understand how to design a modern Identity & Access Management (IAM) strategy that strengthens security without slowing productivity. You’ll learn how to reduce operational friction, gain real-time visibility into access behavior, and meet regulatory requirements—without requiring an enterprise-scale security budget.Write your text here...
Why IAM Is the New Security Perimeter
Write your text here...IAM is no longer just a support system—it is the foundation of zero-trust security and business agility. In 2026, organizations that succeed will be those that treat identity as the new perimeter. This guide breaks down the strategic framework and practical implementations that matter most, helping you stay secure, compliant, and competitive in a threat-driven digital landscape.
Section 2: Understanding Modern IAM Strategy


In today’s hyper-connected digital landscape, Identity and Access Management (IAM) has become the foundation of enterprise security. As organizations accelerate cloud adoption, remote work, SaaS usage, and API-driven architectures, identity—not the network perimeter—has emerged as the primary control plane. Understanding how modern IAM strategies work is essential for building resilient, scalable, and compliant security frameworks.
Subsection 2.1: Why Traditional Access Control Fails Today
Most organizations still rely on legacy access control models that were designed for a very different era—one dominated by on-premises servers, fixed job roles, and clearly defined network boundaries. In 2025, these assumptions no longer hold true, creating serious security and governance gaps.
1. Permission Bloat
One of the most common failures of traditional access control is permission bloat. Employees change roles, projects, and responsibilities over time, yet their old permissions are rarely revoked. As a result:
Users accumulate excessive access rights
Privileges extend far beyond actual job requirements
Attack surfaces grow silently over time
This violates the principle of least privilege and significantly increases the blast radius if an account is compromised.Write your text here...
2. Insider Risk and Credential Abuse
Traditional models assume that authenticated users are trustworthy. However, modern attacks increasingly rely on stolen or compromised credentials. When an attacker gains access to a legitimate employee account, they inherit the same level of trust as the user—often without triggering alerts.
This makes insider threats, both malicious and accidental, extremely difficult to detect using legacy access controls alone.Write your text here...
3. Supply Chain and Machine Identity Exposure
In modern IT environments, machine identities—such as APIs, service accounts, bots, and IoT devices—now outnumber human users by nearly three to one. Unfortunately, many organizations:
Do not maintain an inventory of non-human identities
Use hard-coded credentials that never expire
Lack ownership and lifecycle management
A single unmanaged service account can become a hidden escalation path into critical systems. In many breach investigations, these identities are discovered only after damage has already occurred.Write your text here...
Subsection 2.2: The Shift to Identity-First Security Postures
Write your text here...To address these challenges, organizations are shifting from a “secure the perimeter” mindset to an identity-first security model. This approach assumes that no user, device, or system should be trusted by default—regardless of location.
At the core of modern IAM strategy are three foundational pillars.
1. Identity Inventory and Classification
You cannot protect what you cannot see. Modern IAM begins with creating a complete identity inventory, including:
Human users (employees, contractors, partners)
Machine identities (APIs, workloads, automation scripts)
B2B and third-party identities
Each identity must be classified based on risk, access level, and business function. This visibility enables better governance, auditing, and access decisions.
2. Continuous Verification
Modern IAM replaces one-time authentication with continuous verification. Instead of trusting a user after login, systems continuously evaluate signals such as:
Device posture
Location anomalies
Behavioral patterns
Session activity
If risk increases during a session, access can be restricted or re-authenticated dynamically.
3. Privilege Minimization
Access should be granted only when needed and only for as long as needed. Privilege minimization ensures that:
Standing administrative access is eliminated
Privileged access is time-bound and approval-based
Permissions are revoked immediately after use
These three pillars work together. Without inventory, verification is incomplete. Without governance, privilege minimization is impossible. A modern IAM strategy depends on aligning all three.
Subsection 2.3: Guidance on IAM Strategy and Security – Building Your Framework
A successful IAM program requires a structured, phased approach rather than a one-time deployment. Below is a practical framework organizations can follow.
Step 1: Current State Assessment
Begin by understanding where you stand today.
Catalog existing access control models (RBAC, ABAC, manual approvals)
Identify high-risk systems such as payment platforms, customer PII repositories, and intellectual property stores
Assess visibility gaps—systems without proper audit logging
Document compliance requirements based on industry regulations (ISO, SOC 2, PCI DSS, HIPAA, etc.)
This assessment establishes a baseline for improvement.
Step 2: Future State Design
Next, define what “good” looks like.
Design role-based access templates aligned with real job functions
Define risk-scoring criteria using contextual signals (location, device, behavior)
Establish approval workflows for privileged and sensitive access
Plan an integration architecture that supports cloud, on-premises, and SaaS environments
The goal is to build a flexible, scalable IAM architecture—not a rigid one.
Step 3: Phased Implementation Roadmap
Implementing IAM in phases reduces risk and improves adoption.
Phase 1 (Months 1–3):
Deploy a centralized Identity Provider (IdP)
Enable Single Sign-On (SSO)
Enforce Multi-Factor Authentication (MFA) for critical systems
Phase 2 (Months 4–6):
Implement role-based access controls
Conduct regular access reviews
Phase 3 (Months 7–12):
Activate adaptive authentication for high-risk applications
Introduce conditional access policies
Phase 4 (Months 13–18):
Extend zero-trust principles across all applications
Integrate machine identity governance
Step 4: Governance and Ongoing Monitoring
IAM is not a “set and forget” system.
Conduct quarterly access reviews
Deploy identity analytics to detect anomalies
Create incident response playbooks for suspicious access activity
Integrate IAM telemetry into SIEM and SOC workflows
Strong governance ensures long-term security, compliance, and operational efficiency.
Section 3: Adaptive Authentication in IAM Explained

Adaptive Authentication is rapidly becoming a core pillar of modern Identity & Access Management (IAM). As cyber threats grow more sophisticated and remote work becomes the norm, organizations can no longer rely on static login methods. This section explains adaptive authentication in a practical, real-world, and SEO-friendly way, helping both technical and non-technical readers understand why it matters.
Subsection 3.1: Core Concept – What Is Adaptive Authentication?
Adaptive Authentication is an intelligent, context-aware security mechanism that dynamically decides how much identity verification is required for a login attempt—in real time.
Instead of treating every login as equally risky, adaptive authentication evaluates the context and behavior surrounding each access request. Based on that risk level, the system either allows seamless access or enforces additional security checks.
In simple terms:
Low risk = less friction
High risk = stronger verification
This approach improves security without harming user experience, which is critical for modern digital businesses.
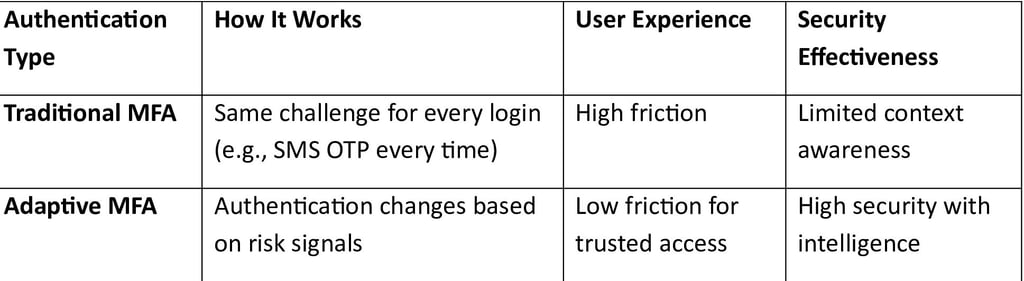
Traditional Authentication vs Adaptive Authentication
Real-World Example
Imagine an employee accessing company systems:
Normal behavior:
Same laptop
Same office location
Business hours
Known applications
👉 Result: Instant access, no extra authentication
Suspicious behavior:
Login from a new country
Unknown device
3:00 AM access attempt
👉 Result: Step-up authentication or session block
This ability to adapt dynamically is what makes adaptive authentication far superior to static login models.
Subsection 3.2: How Adaptive Authentication Evaluates Risk
At the heart of adaptive authentication is a risk assessment engine. This engine evaluates multiple signals in milliseconds and assigns a risk score to each login attempt.
Signal Category 1: Behavioral Signals
Behavioral analysis helps identify whether the user’s activity aligns with historical patterns:
Is the login location familiar?
Does the access time match usual working hours?
Are the applications accessed relevant to the user’s role?
Is the volume of data requested normal?
Unusual behavior does not automatically mean malicious activity—but it raises risk confidence.
Signal Category 2: Device Signals
Device trust plays a critical role in identity verification:
Is the device previously registered or trusted?
Is the operating system updated?
Are security controls like antivirus and disk encryption enabled?
Is this a managed corporate device or a personal one?
A compromised or unknown device significantly increases the risk score
Signal Category 3: Network Signals
Network context adds another layer of protection:
Is the IP address known for malicious activity?
Is the user connected via a corporate VPN or public Wi-Fi?
Does the geographic location make sense compared to the last login?
Are there signs of a compromised network?
Impossible travel scenarios (e.g., India to Europe in 10 minutes) are strong risk indicators.
Signal Category 4: Threat Intelligence Signals
Threat intelligence connects authentication decisions with global cyber threat data:
Have the credentials appeared in known data breaches?
Is the IP associated with credential stuffing attacks?
Are phishing campaigns targeting this industry?
Has the account been flagged in threat intelligence feeds?
This allows IAM systems to react proactively, not just defensively.
The Decision Engine Explained
Once all signals are evaluated, the system generates a risk score (0–100):
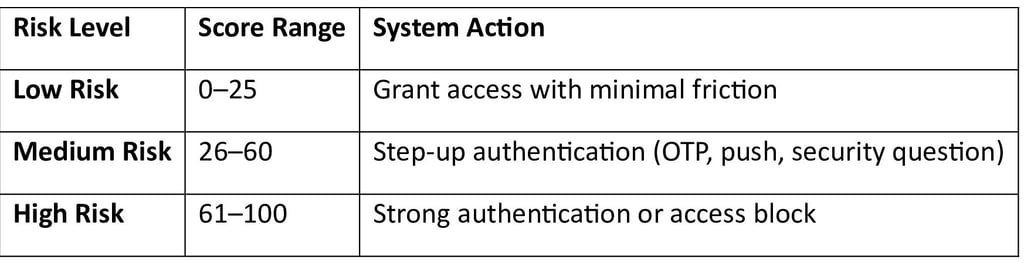
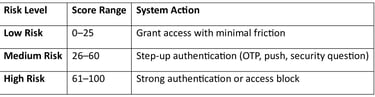
This entire process happens in real time, ensuring security without slowing productivity.
Subsection 3.3: Real-World Deployment Scenarios
Scenario A: SMB with Limited IT Resources
A 50-person marketing agency adopts adaptive authentication using a cloud identity provider like Okta or Azure AD.
Implementation approach:
Passwordless login using passkeys (WebAuthn)
Adaptive MFA enabled only for high-risk events
Result:
80% of logins are frictionless
Suspicious access attempts blocked automatically
Reduced IT workload and support tickets
Scenario B: Regulated Enterprise with Compliance Requirements
A 2,000-employee fintech company operating under PSD2 and SOX regulations implements adaptive authentication with continuous session monitoring.
Key features:
Re-authentication when sensitive financial data is accessed
Automated audit logging
Risk-based access enforcement
Result:
Strong regulatory compliance
Clear audit trails
Reduced insider and external threat exposure
Scenario C: Hybrid Cloud & On-Premises Environment
A healthcare organization managing HIPAA-regulated patient data across cloud and legacy systems deploys adaptive authentication consistently.
Security model:
Hardware tokens for privileged healthcare administrators
Faster authentication for routine staff access
Unified risk evaluation across all environments
Result:
Lower insider threat risk
Improved clinician productivity
Strong protection of patient data
Subsection 3.4: Implementation Best Practices for Adaptive Authentication
Practice 1: Establish Behavioral Baselines First
Run adaptive authentication in monitor-only mode for 2–4 weeks.
This helps identify normal user behavior and avoids false positives that frustrate users.
Practice 2: Prioritize Privileged Access
Start with:
Admin accounts
Financial systems
Customer databases
Once stable, expand adaptive authentication to all users.
Practice 3: Integrate Threat Intelligence
Connect IAM systems with industry threat feeds.
Automatically tighten authentication policies when active attacks are detected.
Practice 4: Design Secure Fallback Procedures
False positives can happen. Provide:
Manager-approved temporary access
Alternative device verification
Secure recovery workflows
This balances security and usability.
Practice 5: Measure and Refine Continuously
Track key IAM metrics:
Step-up authentication rate
False positive incidents
Blocked attack attempts
Use insights to fine-tune policies quarterly.
Subsection 3.5: AI and Machine Learning Integration
Artificial Intelligence transforms adaptive authentication from rule-based security into predictive identity protection.
Key AI Capabilities
Machine Learning Models
Detect subtle anomalies across millions of login events.Behavioral Profiling
Build unique identity patterns for each user.Predictive Threat Detection
Identify compromised accounts before breaches occur.Adaptive Feedback Loops
Learn from past false positives to improve accuracy automatically.
AI-powered adaptive authentication significantly reduces account takeover risk while maintaining seamless user experiences.
Section 4: Implementing IAM Best Practices – A Tactical Playbook for 2026


As cyber threats become more identity-centric, Identity and Access Management (IAM) is no longer a backend IT function—it is a core security strategy. In 2026, attackers are not “hacking systems”; they are abusing identities. This makes IAM best practices a non-negotiable requirement for organizations of all sizes, from startups to regulated enterprises.
This section provides a practical, implementation-ready IAM playbook, aligned with modern compliance frameworks and optimized for real-world business outcomes, especially for SMBs.
Subsection 4.1: The Five Non-Negotiable IAM Practices for 2026
1. Enforce Passwordless Authentication
Passwords are the weakest link in modern security. Phishing, credential stuffing, and password reuse continue to be the leading causes of breaches. In 2026, passwordless authentication is no longer optional—it is a baseline security control.
Organizations should eliminate password reliance wherever technically feasible and adopt FIDO2/WebAuthn standards, which use cryptographic keys stored securely on user devices. This approach prevents phishing entirely because credentials are never shared or transmitted.
Biometric verification—such as fingerprint or facial recognition—adds another layer of protection while improving user experience. However, passwordless does not mean “authentication-free.” Multi-factor authentication (MFA) must still be enforced for all users, including vendors, contractors, and API service accounts.
A phased rollout is the most effective strategy. Start with high-risk access points, such as administrators and finance systems, then expand across the organization. This minimizes disruption while delivering immediate risk reduction.
2. Grant Just-in-Time (JIT) Access
One of the biggest IAM mistakes organizations still make is granting standing access—permanent permissions that users don’t always need. These dormant privileges become prime targets for attackers.
Just-in-Time (JIT) access eliminates this risk by provisioning elevated privileges only when required and automatically revoking them once the task is completed. This significantly reduces the attack surface and ensures compromised credentials are far less useful to attackers.
JIT access is especially critical for privileged roles such as system administrators, DevOps engineers, and database managers. Privileged Access Management (PAM) platforms like CyberArk or HashiCorp Vault enable secure session-based access, credential rotation, and full audit logging.
The result is better security, easier compliance, and reduced internal misuse—without slowing down productivity.
3. Centralize Identity via Federation
Modern organizations operate across cloud platforms, on-premises systems, and dozens of SaaS applications. Without centralized identity control, this creates fragmented access policies and shadow IT risks.
Federated identity solves this by deploying a single Identity Provider (IdP) as the authoritative source for authentication and authorization. Users authenticate once, and access is securely extended across systems based on defined policies.
Centralized federation also enables secure B2B collaboration, allowing organizations to extend access to partners without creating unmanaged local accounts.
Platforms such as Microsoft Entra ID, Okta, Ping Identity, and open-source IdPs provide consistent policy enforcement, simplified user lifecycle management, and easier compliance audits—all from one control plane.
4. Monitor and Detect Continuously
IAM is not “set and forget.” Identities must be continuously monitored to detect misuse, compromise, or abnormal behavior.
Organizations should deploy User Behavior Analytics (UBA) and identity threat detection tools that analyze login patterns, access behavior, and privilege usage in real time. These insights should be correlated with SIEM and SOC workflows for full threat visibility.
Key indicators to monitor include:
Multiple failed login attempts
Access from impossible geographic locations
Unusual data downloads
Off-hours privileged access
Lateral movement between systems
Modern identity threat detection platforms such as Authomize, Netwrix, and Rezonate help security teams respond faster—before minor anomalies escalate into major breaches.
5. Enforce Least Privilege at Scale
The principle of least privilege ensures users can access only what they need—and nothing more. However, enforcing this manually does not scale.
Organizations must conduct regular privilege audits, ideally quarterly or more frequently in high-risk environments. Standing admin rights should be removed and replaced with JIT provisioning.
Advanced environments should adopt Attribute-Based Access Control (ABAC), which evaluates access decisions using context such as role, device posture, location, and risk level.
Identity analytics and visualization tools help security teams detect privilege sprawl and validate compliance continuously—ensuring access aligns with business roles at all times.
Subsection 4.2: Applying IAM to Compliance Frameworks
IAM is a foundational control across all major regulatory frameworks. Instead of treating compliance as a checkbox exercise, organizations should align IAM practices directly with regulatory requirements:
GDPR: Least privilege, access transparency, and automated audit logs support data minimization and accountability.
HIPAA: Role-based access control and MFA protect electronic protected health information (ePHI).
SOX: Segregation of duties and approval workflows prevent financial fraud.
PCI DSS: JIT access and strong authentication restrict access to cardholder data.
NYDFS / DORA: Adaptive MFA and privileged monitoring enable faster incident detection and response.
This alignment reduces audit friction and strengthens overall security posture.
Subsection 4.3: Cost-Benefit Analysis for SMBs
A common misconception among small and medium businesses is that IAM is too expensive. In reality, not implementing IAM is far more costly.
Realistic IAM Costs:
Cloud-based IAM platforms: $5–15 per user per month
Managed IAM services: 15–25% of IT budget for full deployment, monitoring, and compliance support
The Hidden Cost of Inaction:
According to IBM’s 2025 data, the average cost of a data breach is $4.29 million. Even a smaller breach affecting 1,000 customer records can result in hundreds of thousands in losses, regulatory penalties, and long-term brand damage.
ROI Example:
A 100-employee SMB spending $1,500 per month on IAM invests $18,000 annually. Preventing just one moderate breach can save over $400,000, delivering a massive return on investment.
In reality, similar-sized organizations experience security incidents every 2–3 years, making IAM not just affordable—but essential.
Section 5: Emerging Trends & Future-Proofing Your IAM Strategy

Identity & Access Management is no longer a static security control. As cyber threats become faster, smarter, and more automated, IAM must evolve from a reactive system into a predictive, intelligence-driven security layer. Organizations that fail to modernize IAM will struggle with breaches, compliance failures, and poor user experience.
This section explores the most important IAM trends shaping the next decade and explains how businesses can future-proof their identity infrastructure today.
5.1 AI-Powered Risk Engines: From Rules to Prediction
Traditional IAM systems rely heavily on static, rule-based authentication policies. For example, “If the user logs in from a new country, require MFA.” While effective in the past, rule-based models are limited because attackers now mimic legitimate user behavior.
AI-powered risk engines represent the next evolution of adaptive authentication. Instead of reacting to predefined rules, these systems analyze massive behavioral datasets in real time—including device fingerprints, typing patterns, login velocity, network reputation, and historical access behavior.
Using machine learning, modern IAM platforms can predict breach probability before an incident occurs. If a login session deviates subtly from a user’s normal behavior, the system dynamically adjusts security controls—triggering step-up authentication, restricting access, or terminating the session altogether.
From an SEO and business perspective, this shift enables organizations to reduce false positives, improve user experience, and dramatically lower account takeover risk. AI-driven IAM transforms identity from a gatekeeper into a real-time security decision engine.
5.2 Passwordless + Adaptive MFA Convergence
Passwords remain one of the weakest links in cybersecurity. Phishing, credential stuffing, and password reuse continue to fuel the majority of breaches. As a result, passwordless authentication is rapidly gaining adoption.
Passwordless methods—such as biometrics, hardware security keys (FIDO2), and device-based authentication—eliminate shared secrets entirely. However, passwordless alone is not enough. The real power emerges when passwordless authentication is combined with adaptive multi-factor authentication (MFA).
This convergence creates a phishing-resistant and low-friction access model. Low-risk logins can remain seamless, while high-risk scenarios automatically invoke stronger verification. The result is a balance between security and usability—critical for workforce productivity, customer retention, and compliance.
From a monetization standpoint, passwordless IAM content performs well in AdSense because it attracts enterprise buyers, CISOs, and IT decision-makers, all of whom drive high-value CPC keywords.
5.3 Machine Identity Governance: Securing the Non-Human Majority
One of the most overlooked IAM risks today is machine identity sprawl. APIs, service accounts, bots, containers, and IoT devices now outnumber human users by more than 3:1 in most cloud environments.
Unlike human users, machine identities often lack visibility, ownership, and lifecycle controls. Hard-coded credentials, long-lived secrets, and excessive privileges create silent attack paths that bypass traditional security monitoring.
Modern IAM frameworks are expanding to include machine identity governance. This involves:
Discovering and inventorying non-human identities
Assigning least-privilege access policies
Automating credential rotation and expiration
Continuously monitoring machine behavior for anomalies
Securing machine identities is no longer optional. As organizations adopt DevOps, microservices, and multi-cloud architectures, IAM must treat machines as first-class identities.
5.4 Preparing for Post-Quantum Cryptography
Quantum computing introduces a long-term but serious threat to identity security. Current encryption algorithms—used for authentication tokens, certificates, and secure communications—will eventually become vulnerable to quantum attacks.
The most dangerous scenario is known as “harvest now, decrypt later.” Attackers can steal encrypted identity data today and decrypt it in the future once quantum capabilities mature.
Forward-thinking organizations are already testing post-quantum cryptography (PQC) within IAM systems. This includes experimenting with quantum-resistant algorithms, hybrid encryption models, and crypto-agility frameworks.
While widespread quantum attacks may still be years away, IAM leaders who prepare early will avoid costly migrations and compliance risks later.
5.5 Identity Orchestration Platforms: The Future of IAM
The future of IAM is not more tools—it is orchestration. Many organizations struggle with fragmented identity solutions across cloud, on-premises, SaaS, and legacy systems.
Identity orchestration platforms unify access decisions across environments in real time. Instead of relying on disconnected point tools, these platforms coordinate authentication, authorization, risk signals, and policies through a centralized identity fabric.
This approach enables:
Consistent zero-trust enforcement
Faster security response
Simplified compliance reporting
Scalable hybrid and multi-cloud access control
Identity orchestration is rapidly becoming the backbone of next-generation IAM architecture.
Section 6: Conclusion & Call-to-Action
Recap: The IAM Evolution
Modern Identity & Access Management has evolved far beyond usernames and passwords. AI-powered risk engines, adaptive authentication, passwordless access, machine identity governance, and identity orchestration now work together to create a security posture that is both stronger and more user-friendly than legacy models.
IAM is no longer just an IT function—it is a business enabler that protects data, ensures compliance, and supports digital transformation.
Primary Takeaway
Identity is the new perimeter.
Organizations that master IAM strategy, enforce least-privilege access, and deploy adaptive authentication can reduce breach risk by up to 85%, while enabling secure, agile operations across cloud and hybrid environments.
Call-to-Action
To take the next step in strengthening your IAM posture, choose one of the following:
Download a Free IAM Maturity Assessment Tool
Identify gaps in your identity security and benchmark against industry best practices.Compare IAM Solutions
Explore in-depth comparisons such as Okta vs Microsoft Entra to find the right platform for your organization.Subscribe to Security Updates
Stay informed with expert insights on IAM trends, compliance, and emerging threats.
Follow The TAS Vibe for the latest technology insights. For company promotions or advertising opportunities, please contact us at: raytanmoy88264@gmail.com
Connect
Stay updated with us
Follow
Reach
+91 7044641537
© 2025. All rights reserved.
